This article was written in Korean and then translated into English, so there may be inaccuracies.
Hello,
I set up a WordPress blog yesterday, on 2024.10.06, and it’s already experiencing brute force attacks, haha.
Aside from that, the server went down once as well… (After checking the syslog, it seems like it could be an AWS authentication issue…)
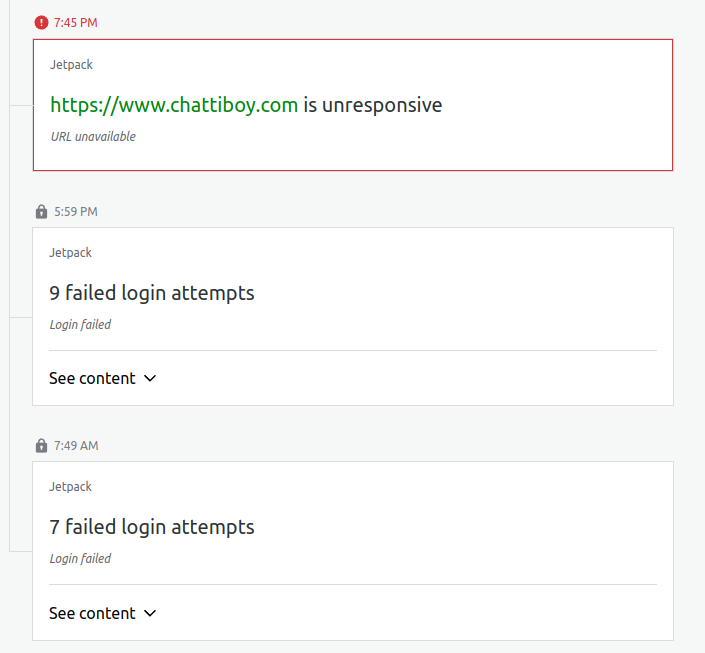
Anyway, since the site is under attack, I need to check it out, right?
In my case, I have HAProxy in front of WordPress, so HAProxy is acting as a firewall.
Cause of the Attack
When I checked. why there were brute force login attempts?
I check blocked
“https://www.chattiboy.com/wp-admin”.
But, some page was still open…
“https://www.chattiboy.com/wp-login.php”
I didn’t even know this existed until I got attacked today, haha.
Setting Access Restriction Policies
Now that I know the cause, I need to block it, right?
This can easily be blocked with a simple HAProxy configuration.
(You can also set it up for redirection!)
frontend haproxy.front
mode http
bind :80
bind :443 ssl crt /home/chattiboy/ssl-list
redirect scheme https code 301 if !{ ssl_fc }
# Block all IPs defined in the blacklist.
acl blacklist src -f /etc/haproxy/blacklist_addrs.list
http-request deny if blacklist
# Block all paths starting with `/admin/`.
http-request deny if { path -i -m beg /admin/ } !{ src 192.168.0.0/24 }
http-request deny if { path -i -m sub /wp-admin } !{ src 192.168.0.0/24 }
# Block all paths comprehensively starting with `/wp-login/`.
http-request deny if { path -i -m sub /wp-login } !{ src 192.168.0.0/24 }Allow access only from a specific IP range and block all other access.
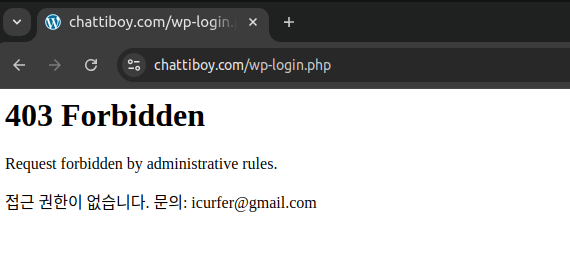
If you’re using Nginx, you can apply a similar blocking policy in the Nginx configuration as well. Blocking is possible, and of course, redirection can be configured too.
We’ve briefly covered URL subpath blocking policies using HAProxy.
